Cyber Risk Assessment
Discover the future of cyber risk management
with CRA, the cutting-edge SaaS solution.
Goodbye to excel,
hello to CRA
Say goodbye to the messiness of Excel and other solutions. CRA provides a safe web-based environment for collaborative risk management. Easily perform risk assessments within the platform, with actionable insights on where to begin reducing your risks. Get a holistic risk overview and embark on proactive risk management.
Unlock Efficiency
And savings
Experience top-tier risk management with CRA, all while optimizing your resource allocation. Its outstanding efficiency means you'll save both time and money, making it a wise investment for your operations.
Overview of Supply
Chain Security
Distribute CRA to your suppliers to gain valuable insights into their cyber risk maturity levels. This transparency not only enhances your supply chain security but also ensures compliance with NIS2 regulations that mandate this level of insight.
Goodbye to excel,
hello to CRA
Say goodbye to the messiness of Excel and other solutions. CRA provides a safe web-based environment for collaborative risk management. Easily perform risk assessments within the platform, with actionable insights on where to begin reducing your risks. Get a holistic risk overview and embark on proactive risk management.
Unlock Efficiency
And savings
Experience top-tier risk management with CRA, all while optimizing your resource allocation. Its outstanding efficiency means you'll save both time and money, making it a wise investment for your operations.
Overview of Supply
Chain Security
Distribute CRA to your suppliers to gain valuable insights into their cyber risk maturity levels. This transparency not only enhances your supply chain security but also ensures compliance with NIS2 regulations that mandate this level of insight.
HOW IT WORKS
Dive into CRA today and transform your risk management
processes, making them more efficient and impactful!
5-LEVEL MATURITY
5-LEVEL MATURITY
Maturity Score
Recommended minimum score: 3.0
MATURITY SCORING SYSTEM
CRA comprises a five-tier maturity model, providing a structured approach for breaking down implementation into manageable phases. Additionally, it accommodates business-specific and customized requirements, making it a versatile choice for enhancing cybersecurity.
CRA comprises a five-tier maturity model, providing a structured approach for breaking down implementation into manageable phases. Additionally, it accommodates business-specific and customized requirements, making it a versatile choice for enhancing cybersecurity.
Maturity Score
Recommended minimum score: 3.0
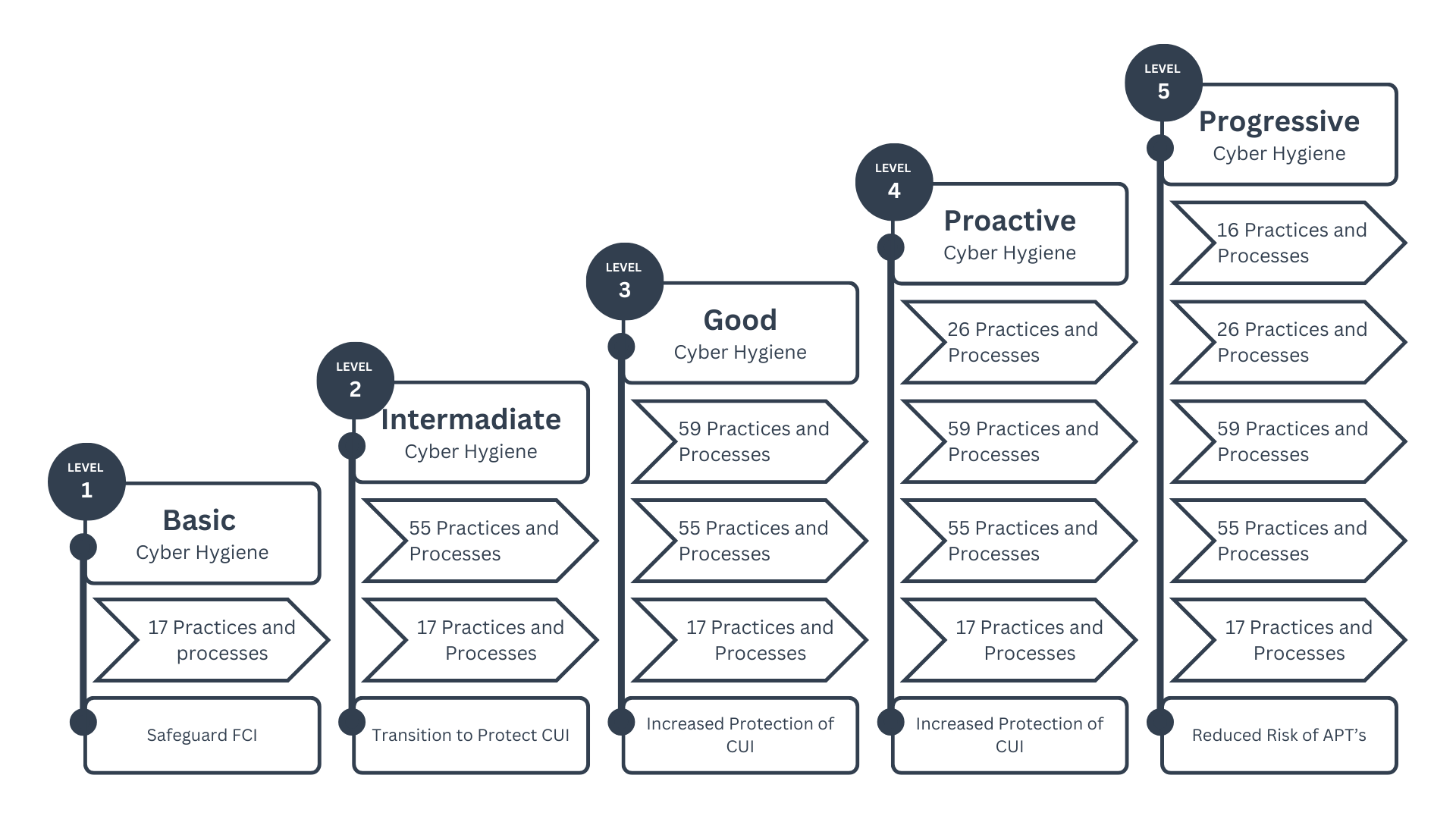
As shown in the image above, each level has a certain number of practices beneath it. Level 1 has 17 practices, level 2 has 72, and it keeps growing up to 171 practices at level 5. This growth happens because the levels build on each other. For instance, to reach level 3 in a specific domain, you also need to show that you've met the requirements for levels 1 and 2.
17 DOMAINS OF
SECURITY PRACTICES
The framework structure
CRA is like a structured guidebook for cybersecurity. Based on the framework CMMC it has 17 sections, called domains, where you can find different security practices. Our software measures these practices based on the five levels of difficulty, from basic to advanced. Each domain also includes specific abilities you need to have, and within those abilities, there are specific actions you must show you can do. It's a way to measure and improve how well you protect your data and systems.
Access Control
Asset Management
Awareness and Training
Audit and Accountability
Configuration Management
Identification and Authentication
Incident Response
Maintenance
Media Protection
Personnel Security
Physical Security
Recovery
Risk Management
Security Assessment
Situational Awareness
Systems and Communications Protection
System and Information Protection
43 CYBER SECURITY
CAPABILITIES
The framework defines 43 cyber security capabilities across the 17 domains. These capabilities involve a combination of processes, skills, knowledge, tools, and behaviors that work together to ensure a specific level of security.
Organizations should aim to achieve these capabilities at the maturity levels 1-5 when they appropriately deploy and manage cyber security practices.
The framework defines 43 cyber security capabilities across the 17 domains. These capabilities involve a combination of processes, skills, knowledge, tools, and behaviors that work together to ensure a specific level of security.
Organizations should aim to achieve these capabilities at the maturity levels 1-5 when they appropriately deploy and manage cyber security practices.
Ex. ACCESS CONTROL has the following associated capabilities:
C001: Establish systems access requirements
C002: Control internal systems access.
C003: Control remote systems access.
C004: Limit data access to authorised users and processes.
Ex. ACCESS CONTROL has the following associated capabilities:
C001: Establish systems access requirements
C002: Control internal systems access.
C003: Control remote systems access.
C004: Limit data access to authorised users and processes.
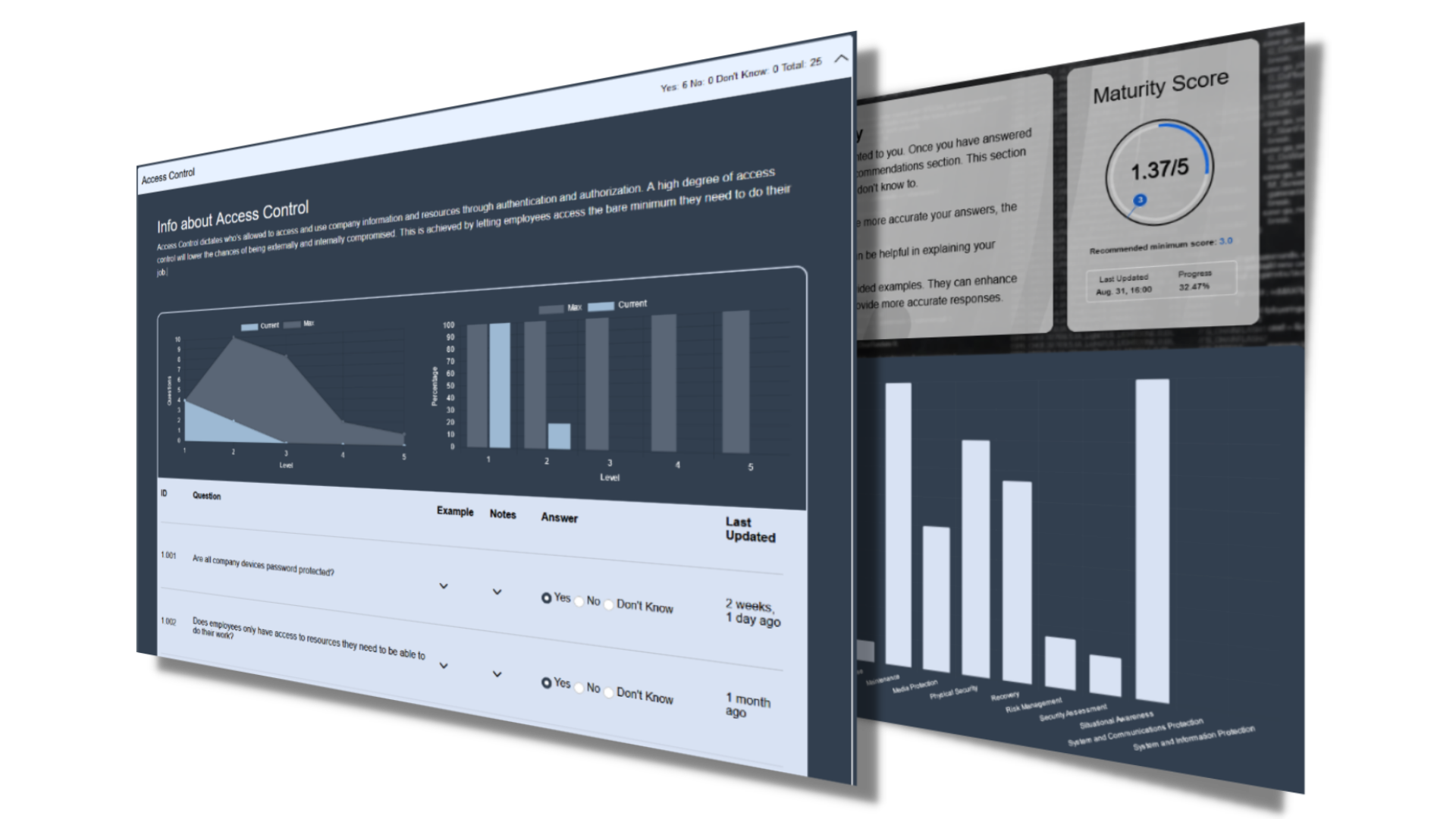
QUESTION & SCORING EXAMPLE - ACCESS CONTROL DOMAIN:
ACCOUNT MANAGEMENT
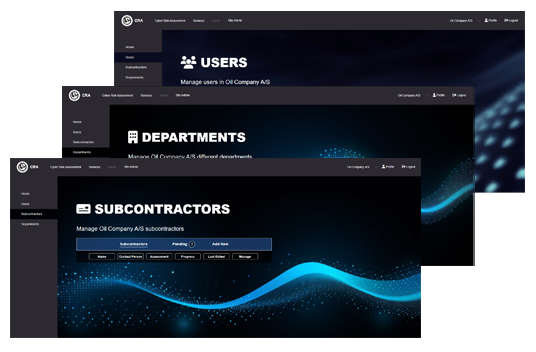
With our user-friendly platform, you can effortlessly create and manage users, departments, and suppliers while gaining a comprehensive overview of your organization's cyber risk landscape, including those suppliers you've invited to collaborate.
Discover how easy it is to enhance your cyber resilience, collaborate seamlessly with suppliers, and take charge of your organization's security.


 Upgrade your account
Upgrade your account